Loading...
Loading...
We run the heavy infrastructure of OpenVAS so you don't have to. Get continuous scanning and risk-based prioritization in minutes.
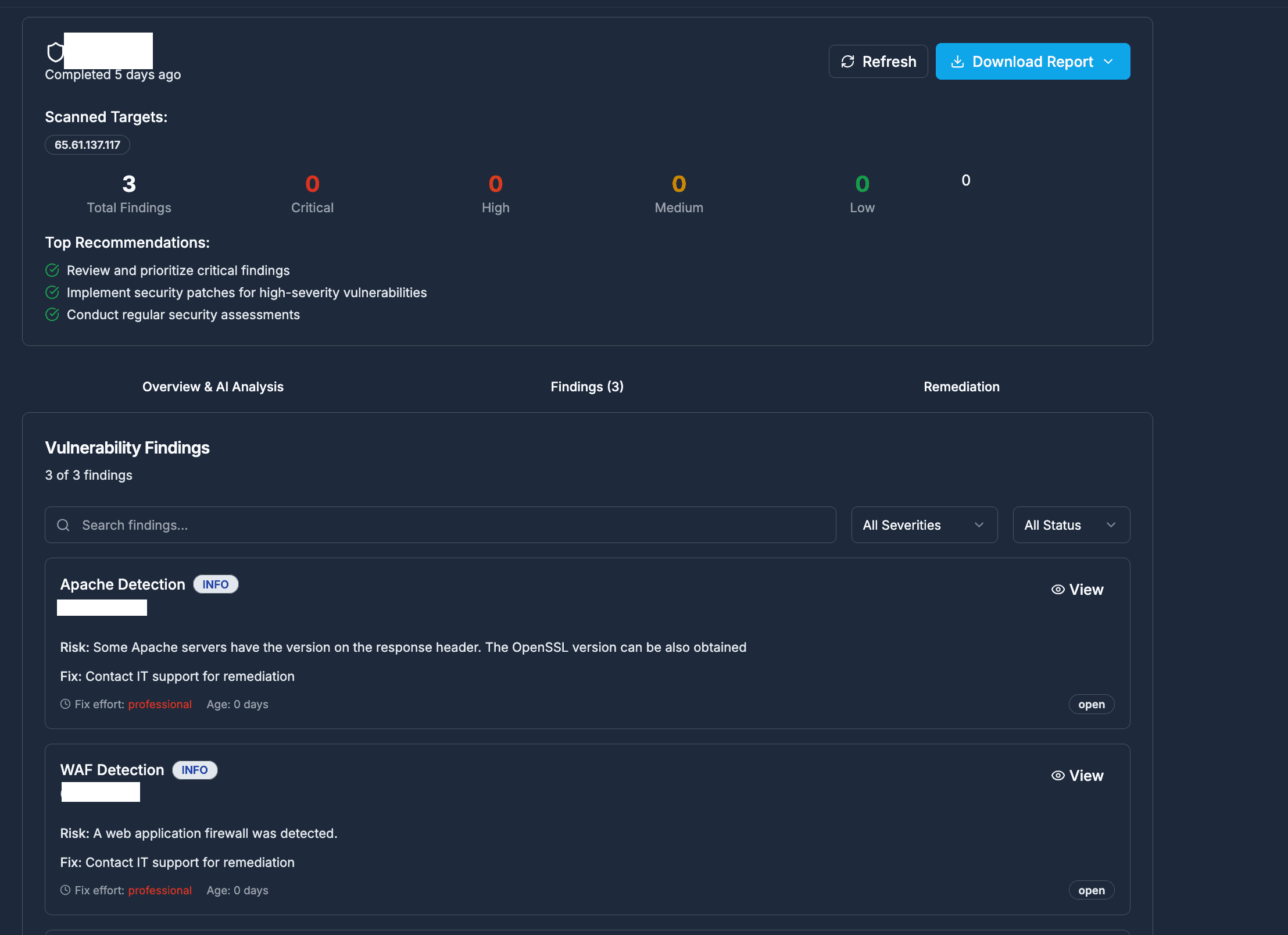
Most vulnerability scanners dump a PDF on your desk and walk away. We use threat intelligence to tell you which vulnerabilities actually matter for your business context.
Network, web apps, databases, and OS configurations.
We highlight "Exploitable" vs just "CVSS High".
Yes. AIOpenSec uses OpenVAS scanning capabilities and manages the heavy lifting (feeds, scheduling, infrastructure) while presenting prioritized, actionable results.
Yes. Authenticated scanning is supported where appropriate, so you can find missing patches and misconfigurations that unauthenticated scans can’t see.
We correlate results with exploit intelligence and context so you focus on what is most likely to be exploited, not just what scores high on CVSS.